How Onchain and Key Image Analysis Make Monero Traceable, Rendering Churning Ineffective
The most difficult part to grasp when studying key image analysis is how pattern analysis is performed. In this article I will touch on the topic of TXO pattern analysis and how it can be used to deanonymize Monero transactions.
TXO Patterns
TXO pattern analysis consists of spotting patterns that allow us to create sets of TXOs and then eventually from these sets we can identify real spends by cross referencing the (number of) key images in each transaction with the pattern forming TXOs. Each TXO in the Monero blockchain appears as output in only one transaction, the birth transaction ID. This transaction is the transaction where the TXO was created and all the metadata of said transaction are effectively tied to the TXO. Here is a list of some onchain TXO metadata:
Each Monero transaction has a timestamp and we can consider this timestamp as the exact creation date of that TXO as it corresponds to when the TXO was engraved into the Monero blockchain. Based on timestamps we could create sets of TXOs created in a specific time of the day, or specific day of the week or a specific month of the year etc.
Sibling TXOs are the other TXOs (outputs) produced as part of the transaction where the TXO in question was created. In general, each Monero transaction has at least 2 outputs so each Monero TXO shares its birth transaction ID with at least another TXO. In case of a transaction with more than two outputs then there will be multiple TXOs that share the same birth transaction ID. Pattern analysis of TXOs can be applied to the number of siblings a specific TXO has (ie: the number of transaction outputs that were created together with it). For example, we could create a set of all TXOs that have three siblings, another one for those with four siblings, ten siblings etc. Another pattern we could look for is by analyzing the future behavior of siblings. For example, we could create a set of all TXOs that were created in two-output transactions and where the other output later always appeared in huge consolidation transactions. A consolidation transaction is a transaction that contains a very high number of key images because the spender is spending many TXOs at once. Monero users resort to consolidation transactions to consolidate fragmented balances into a new single TXO. Consolidation transactions are an inevitable and common behavioral pattern observed in all UTXO blockchains.
The number of inputs in the transaction that created a TXO generates patterns. In every Monero transaction we know the number of inputs spent by the number of key images published in the transaction. Since each TXO is created by a Monero transaction, we can use the number of key images in this transaction as a parameter to spot patterns. This way we compile sets of all TXOs that were created by single input transactions (and call them single input TXOs?); a set for TXOs created by 2 input transactions (two input TXOs?); a set for TXOs created by 3 input transactions, etc.
Fee structure in the birth transaction allows further grouping of TXOs based on fee structure. We compile a set of TXOs created in transactions that shared the same fee, or another set for TXOs created with very high fees (above a certain limit). If we plot the number of transactions against fee value we will probably get a gaussian curve and each slice of the curve would consist of TXOs that share a fee structure pattern.
How to use TXO pattern analysis to find real spends (key image analysis) in Monero transactions
By using onchain patterns we can start identifying TXOs that are likely to be related. We consider two TXOs as related if they share a pattern that is so rare that makes it highly likely for those TXOs to be controlled by the same entity or related entities.
single input transaction (one KI) with periodicity pattern: a transaction is formed today that contains, among inputs, a TXO1 that shows a periodicity pattern. If the period is 1 week, it means that TXO1 was created 1 week ago in another 1 input transaction. And in addition to that, there is one TXO1' among the inputs in the TXO1’s birth transaction that was also created in a single input transaction of one week prior. Doing so we have identified a user that is churning their XMR every 1 week: TXO1' (created in single input transaction) -> seven days later, TXO1 is created in another single input transaction (A) that contains TXO1' among its inputs -> and today, seven days after TXO1's creation, TXO1 appears among the inputs of another single input transaction (B). The presence of this periodicity pattern indicates that TXO1' and TXO1 are the ones being spent in Transaction A and in Transaction B, allowing us to map their key image by bypassing the DDH problem.
multi input transaction (>1 KI) with age-gap TXOs among inputs: if a transaction is formed today that features 2 key images and contains 2 TXOs that were created in Sunday evenings in 2021 then we can be certain that the key images in the transaction belong to the TXOs from 2021. The reason is that the chances of two 2021 TXOs sharing a behavioral pattern being picked by the Monero decoy algorithm are extremely low.
multi input transaction (>1KI) with age-gap TXOs that have unusually consistent fee structure: if a transaction is formed today that shows 2 or more TXOs, created between 2021 and 2023, both of which either have the same fee structure (in the transactions that created them) or a fee structure that is different in each case but consistent with those of known centralized service providers (as defined by onchain activity), then we can reasonably conclude that the key images in today’s transaction belong to the TXOs created between 2021 and 2023 that feature consistent fee structures associated with those of centralised parties.
multi input transaction (>1KI) with sibling patterns: a transaction is formed today that shows two or more TXOs all of which 1) created in the same time range (eg: between 8pm and 9pm UTC) and 2) from two-output transactions; and 3) the sibling of each of these TXOs was later included in multi input transactions with unusually consistent fee structure. We can reasonably conclude that the pattern forming TXOs are being spent and the key images in the transaction formed today belong to them.
Creating a database of burnt TXOs
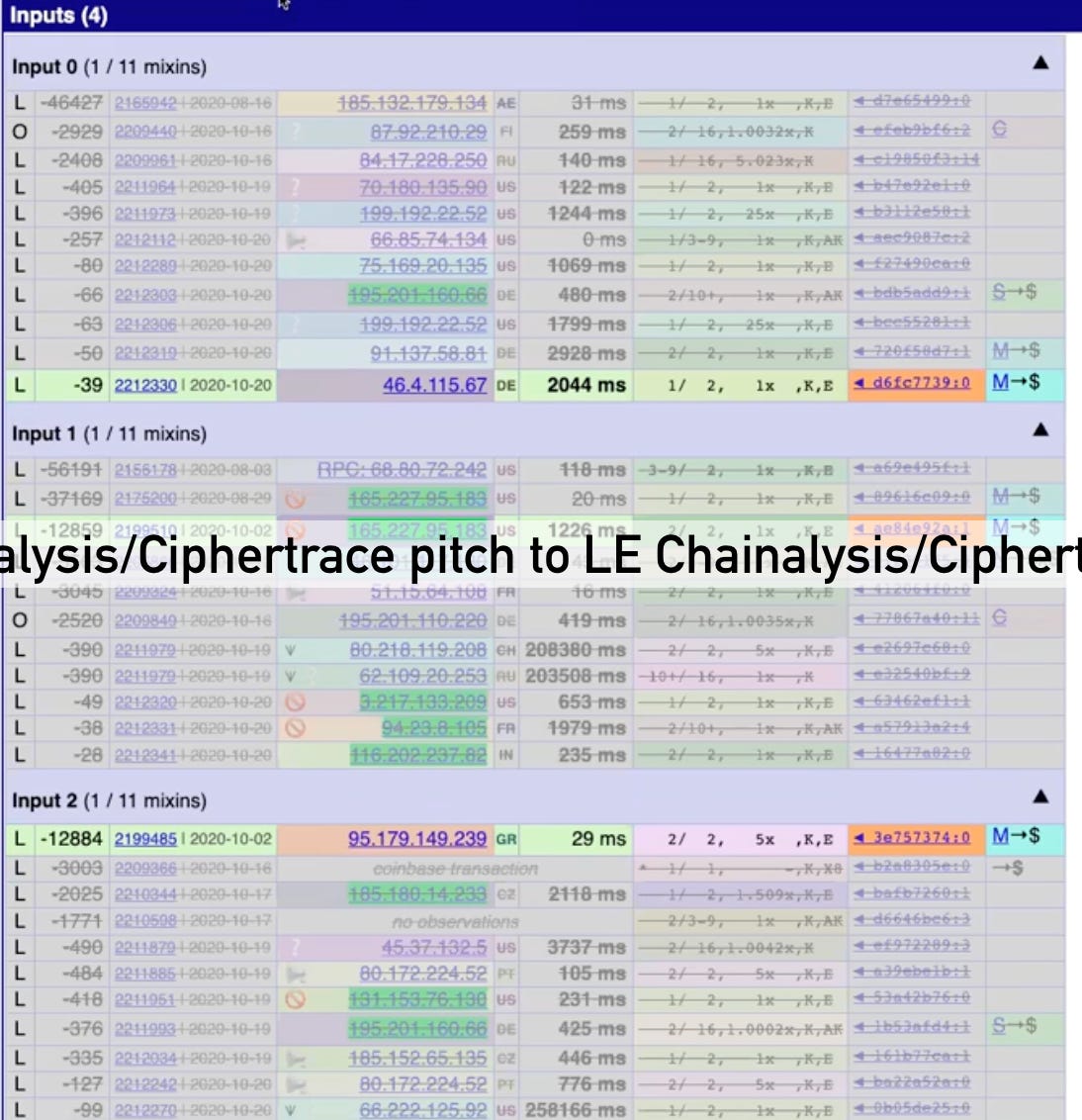
As we’ve seen, by triangulating key images with TXO patterns we can bypass solving the DDH problem and expose the key images of many TXOs even in single input transactions. This way we can compile huge TXO-key image sets to then use to filter out decoys in other transactions. In the real world CEX data makes this process even easier as all CEXes report their transaction activity quarterly to chain analysis firms. For these reasons Monero’s privacy model is to be considered obsolete today, in the era of AI. The recent Chainalysis leak, featuring a tool capable of filtering out 10 of 11 decoys in single input transactions, is further evidence of said obsoleteness.